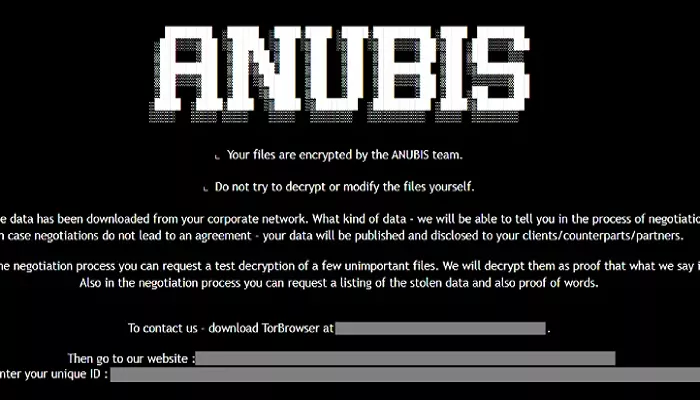
A new ransomware strain has been discovered that not only encrypts files but can also permanently erase them, a feature described as a “rare dual-threat.”
The ransomware, named Anubis, includes a “wipe mode” that permanently deletes files, making recovery impossible even if the ransom is paid. This discovery was made by Trend Micro researchers Maristel Policarpio, Sarah Pearl Camiling, and Sophia Nilette Robles, who published a report on the threat last week.
Anubis, which became active in December 2024, has targeted industries such as healthcare, hospitality, and construction in Australia, Canada, Peru, and the U.S. Researchers found that the ransomware was initially branded as “Sphinx” before being renamed in its final version.
It’s important to note that Anubis is not related to the Android banking trojan or a Python-based backdoor, both of which share the same name and are linked to the financially-motivated cybercrime group, FIN7 (also known as GrayAlpha).
Anubis operates as a ransomware-as-a-service (RaaS) operation, offering flexible affiliate programs with negotiable revenue splits. Affiliates can take 80% of the ransom paid, while data extortion and access sales offer splits of 60-40 and 50-50, respectively.
The attack process begins with phishing emails used to gain initial access. Once the attackers have established a foothold, they escalate privileges, conduct reconnaissance, and delete volume shadow copies before encrypting files. If the victim refuses to pay, the ransomware can use its wipe mode to permanently erase file contents, leaving the files with a 0 KB size while keeping their names and extensions intact, making recovery impossible.
“The ransomware includes a wiper feature using the /WIPEMODE parameter, which can permanently delete the contents of a file, preventing any recovery attempts,” Trend Micro explained. The ability to both encrypt and destroy data increases the pressure on victims to pay the ransom.
This discovery of Anubis’ dual-threat capabilities comes at a time when cybersecurity firm Recorded Future has uncovered new infrastructure linked to the FIN7 group, which is involved in a campaign to deliver the NetSupport RAT (remote access trojan). Recorded Future identified three distribution methods: fake browser update pages, fake 7-Zip download sites, and the TAG-124 malware campaign, all of which use custom loaders to deliver the RAT.
One of the custom loaders, called MaskBat, is designed to execute the RAT and contains strings related to the GrayAlpha group. The malware has been observed through multiple infection vectors, with the fake 7-Zip download pages still active as of April 2025.